From Vulnerable to Vigilant: Transforming Vulnerability Management Processes
I only recently decided to join the Reddit community and actually start contributing to the broader cybersecurity subreddit (aside from also being a prolific reader of the r/dune subreddit). It was there that I stumbled upon a compelling discussion on the challenges of managing the deluge of vulnerabilities identified during quarterly assessments. This dialogue not only resonated with my own experiences but also served as a catalyst for this rehash into an effective vulnerability triage process I have been using to assist organisations – a methodology that leverages both technical acumen and strategic foresight to ensure that remediation efforts are directed where they are most critically needed.
A Brief Snapshot of Vulnerabilities Since 2000
Diving into the data I’ve prepared up until October 2023, we observe a consistent uptick in the number of published CVEs annually. This isn’t just an academic observation; it signifies a mounting pressure on remediation teams and an ever-expanding battlefield for cybersecurity professionals.
While the severity ratings aren’t dissected here, the increasing discovery rates underscore a critical need: the evolution of vulnerability assessment and triage. This includes a shift from the traditional reliance on severity ratings and CVSS Base Scores – metrics that I suggest be de-emphasised in decision-making, unless contractual obligations dictate otherwise.
Exploitable versus Not-Yet/Not-Exploitable Vulnerabilities
Between 10 to 20% of known CVEs are considered potentially exploitable, according to certain security vendor research. Yet, when we examine data from various Vulnerability Intelligence Feeds, a starkly different picture emerges—one where the percentage of exploitability for CVEs dips to between 1 and 5% in recent years. The graph I had shared painted this vividly: the actual count of CVEs ripe for exploitation is a sliver of the total published figures.
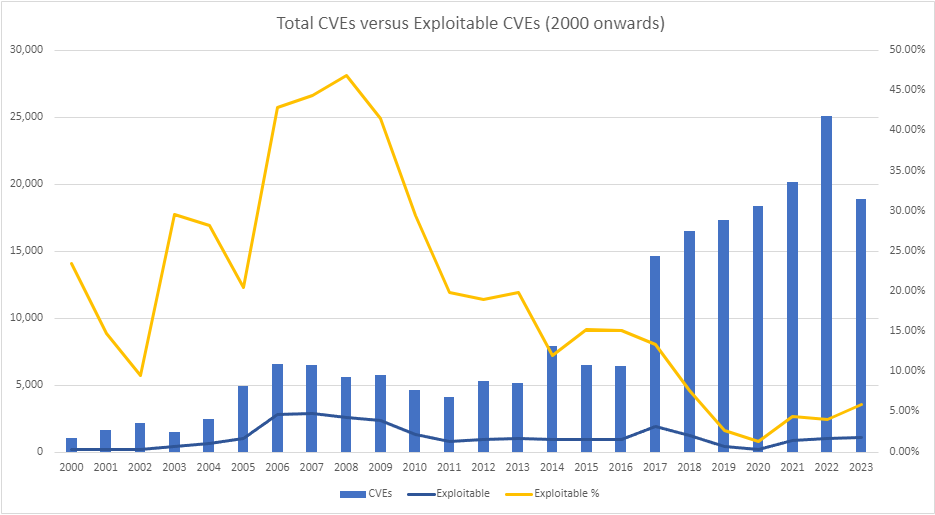
| Year | # of CVEs | # of Est. Exploitable | Exploitable % |
|---|---|---|---|
| 2000 | 1,019 | 240 | 23.55% |
| 2001 | 1,676 | 249 | 14.86% |
| 2002 | 2,156 | 208 | 9.65% |
| 2003 | 1,527 | 452 | 29.60% |
| 2004 | 2,451 | 692 | 28.23% |
| 2005 | 4,932 | 1,014 | 20.56% |
| 2006 | 6,608 | 2,841 | 42.99% |
| 2007 | 6,516 | 2,897 | 44.46% |
| 2008 | 5,632 | 2,645 | 46.96% |
| 2009 | 5,732 | 2,383 | 41.57% |
| 2010 | 4,639 | 1,369 | 29.51% |
| 2011 | 4,150 | 828 | 19.95% |
| 2012 | 5,288 | 1,011 | 19.12% |
| 2013 | 5,187 | 1,034 | 19.93% |
| 2014 | 7,937 | 958 | 12.07% |
| 2015 | 6,487 | 990 | 15.26% |
| 2016 | 6,447 | 977 | 15.15% |
| 2017 | 14,643 | 1,963 | 13.41% |
| 2018 | 16,509 | 1,282 | 7.77% |
| 2019 | 17,305 | 484 | 2.80% |
| 2020 | 18,350 | 251 | 1.37% |
| 2021 | 20,158 | 911 | 4.52% |
| 2022 | 25,101 | 1,023 | 4.08% |
| 2023 | 18,914 | 1,137 | 6.01% |
| Total | 209,364 | 27,839 | 13.30% |
Prioritising Risk Over Severity
This is where the vulnerability management conundrum truly lies—an overdependence on CVSS scores can skew the remediation focus towards less critical vulnerabilities that boast higher severity ratings. Instead, I advocate for a risk management approach that differentiates between severity and organisational risk, allowing for a prioritised approach that zeroes in on the vulnerabilities that pose real-world threats.
A Two-Pronged Approach: KEV and EPSS
Integrating CISA’s KEV catalog and the EPSS into the vulnerability triage process fundamentally changes our battlefield tactics. KEV zeroes in on vulnerabilities under active exploitation, signaling a clear and present danger. Conversely, EPSS uses predictive analytics to spotlight vulnerabilities on the cusp of being exploited, giving us a chance to shore up defences before the storm hits.
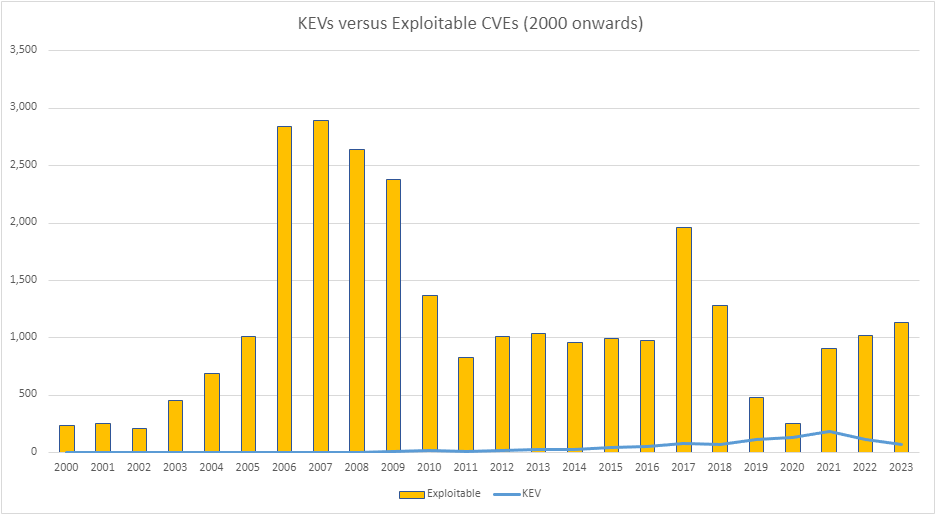
By overlaying these numbers – KEV’s pinpointed vulnerabilities and those with high EPSS scores – we arrive at a much more manageable figure that truly needs immediate attention.
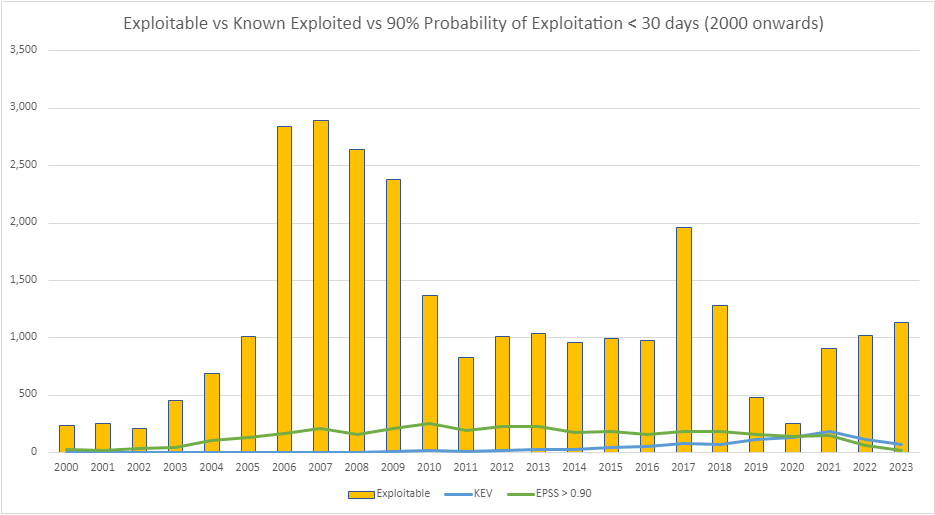
| Year | CVEs | Exploitable | KEV | EPSS > 0.90 |
|---|---|---|---|---|
| 2000 | 1,019 | 240 | 0 | 25 |
| 2001 | 1,676 | 249 | 0 | 20 |
| 2002 | 2,156 | 208 | 1 | 38 |
| 2003 | 1,527 | 452 | 0 | 41 |
| 2004 | 2,451 | 692 | 2 | 103 |
| 2005 | 4,932 | 1,014 | 1 | 134 |
| 2006 | 6,608 | 2,841 | 2 | 168 |
| 2007 | 6,516 | 2,897 | 1 | 212 |
| 2008 | 5,632 | 2,645 | 4 | 161 |
| 2009 | 5,732 | 2,383 | 9 | 208 |
| 2010 | 4,639 | 1,369 | 19 | 254 |
| 2011 | 4,150 | 828 | 8 | 190 |
| 2012 | 5,288 | 1,011 | 20 | 228 |
| 2013 | 5,187 | 1,034 | 31 | 224 |
| 2014 | 7,937 | 958 | 30 | 177 |
| 2015 | 6,487 | 990 | 40 | 182 |
| 2016 | 6,447 | 977 | 51 | 155 |
| 2017 | 14,643 | 1,963 | 81 | 185 |
| 2018 | 16,509 | 1,282 | 67 | 185 |
| 2019 | 17,305 | 484 | 117 | 156 |
| 2020 | 18,350 | 251 | 131 | 143 |
| 2021 | 20,158 | 911 | 187 | 145 |
| 2022 | 25,101 | 1,023 | 117 | 64 |
| 2023 | 18,914 | 1,137 | 69 | 20 |
| Total | 209,364 | 27,839 (13%) | 988 (0.47%) | 3,418 (1.6%) |
It is also worth pointing out, some of the CVEs which were counted in Exploited, EPSS and KEV are duplicated in each metric. Meaning, a CVE does not necessarily exclusively get categorised in only one metric, they may well be within all of them.
Vulnerability Triage
With the universe of CVEs published since 2000 at our disposal, we craft a triage process that filters through the noise:
- CVEs on the KEV list are assessed for immediate relevance and remediation.
- CVEs exceeding our EPSS threshold are evaluated and slated for prompt remediation.
- Theoretically exploitable CVEs are reviewed and scheduled for remediation accordingly.
This prioritisation ensures that our focus is sharp: first on the vulnerabilities that demand immediate national attention, next on those predicted to pose a threat soon, and lastly on those that have the potential for future exploitability.
But What About the CVEs That Get Missed?
No strategy is airtight. KEV and EPSS, though powerful, won’t catch every threat. There will be CVEs that slip through, which is why this strategy is about prioritising your efforts on the ground, creating bandwidth to explore the outliers and less conspicuous vulnerabilities.
For instance, CVE-2023-26083 demonstrates the essence of this approach – not to provide exhaustive coverage but to streamline focus, allowing for the investigation into such anomalies. It’s about strategic allocation of time and resources, ensuring we remain vigilant and adaptable in an evolving threat landscape.
CVE-2023-26083 (Low) Memory leak vulnerability in Mali GPU Kernel Driver
CVE-2023-26083 (Low) CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N
Memory leak vulnerability in Mali GPU Kernel Driver in Midgard GPU Kernel Driver all versions from r6p0 – r32p0, Bifrost GPU Kernel Driver all versions from r0p0 – r42p0, Valhall GPU Kernel Driver all versions from r19p0 – r42p0, and Avalon GPU Kernel Driver all versions from r41p0 – r42p0 allows a non-privileged user to make valid GPU processing operations that expose sensitive kernel metadata.
At the time that I presented these statistics, CVE-2023-26083 was considered a Low (Base Score 3.3) severity vulnerability with an EPSS of 0.001 (that is less than 1% chance). The vulnerability was published on the 6th of April 2023 to NVD and was followed by a CISA Binding Operational Directive on the 7th of April 2023 to “apply updates per vendor instructions” within 21 days. EPSS still to date (11th of April 2024) rates the CVE as a 6.1% chance of becoming exploited in the next 30 days (Effectively EPSS is unaware of the CISA KEV rating).
What we now know is that CVE-2023-26083 was exploited as part of a chain of vulnerabilities by a spyware vendor targeting vulnerabilities on Android devices.
Beyond Triage: A Holistic Vulnerability Management Strategy
Adopting KEV and EPSS is just the beginning of a comprehensive vulnerability triage strategy. Effective triage leading into management also encompasses:
- Asset Categorisation: A deep understanding of the organisation’s IT ecosystem is crucial. By categorising assets based on their exposure and accessibility, remediation efforts can be focused on protecting the most critical or vulnerable systems.
- Roles and Responsibilities: Clearly defined risk ownership and remediation responsibilities ensure accountability and facilitate effective vulnerability management. This clear delineation of roles aids in the efficient addressing of identified vulnerabilities.
- Diversifying Sources: Relying on a single source for vulnerability information can lead to oversight. Utilising diverse sources, including direct reports from CVE Numbering Authorities (CNAs), provides a comprehensive view of vulnerabilities and their implications.
- Effective Communication: Translating technical vulnerabilities into business risks is essential for aligning cybersecurity initiatives with organisational objectives. Effective communication ensures that decision-makers understand the implications of vulnerabilities, leading to informed risk management decisions.
Delving Deeper: My Journey Through Vulnerability Assessment and Triage
In my explorations and contributions within the cybersecurity community, I’ve traversed a wide range of topics, each adding a layer of depth to the complex tapestry of vulnerability assessment and management. Here, I delve into the essence of these topics, sharing my insights and experiences on refining cybersecurity strategies. These reflections form a series of deep dives into the components crucial for an all-encompassing approach to vulnerability management.
- Introduction to Effective Vulnerability Management: Beyond the Basics
Transitioning from a severity-based model to a risk-focused methodology marked a pivotal shift in my approach to vulnerability management. Recognising that not all vulnerabilities equate to the same level of risk across different environments, I advocated for a strategy that prioritises real-world risk over theoretical severity. This post lays the foundation for a series that aims to unravel the intricacies of an effective vulnerability management strategy, guided by the principle of prioritising tangible risks. - Asset Categorisation in Vulnerability Management: Identifying Your Digital Crown Jewels
Following the establishment of a robust risk management framework, my focus shifted to the critical process of asset categorisation. I discussed the strategic importance of identifying and categorising assets based on their exposure and criticality. This approach not only aids in prioritising remediation efforts but also ensures that resources are efficiently allocated to protect the most significant assets, our digital crown jewels. - The Role of Risk Owners and Remediation Teams in Securing Your Assets
The clarity of roles within the vulnerability management process is paramount. I explored the essential roles of risk owners and remediation teams in ensuring a streamlined and effective response to vulnerabilities. Assigning clear responsibilities and fostering collaboration between these roles amplifies the effectiveness of vulnerability management efforts, enhancing the organisation’s overall security posture. - Rethinking CVSS: Prioritising Remediation with KEV and EPSS Scores
Moving beyond the conventional CVSS scores to a more nuanced prioritisation approach became a cornerstone of my strategy. I discussed integrating Known Exploited Vulnerabilities (KEV) and Exploit Prediction Scoring System (EPSS) scores to focus remediation efforts on vulnerabilities posing the most immediate and significant threats. This approach aligns remediation priorities with the evolving threat landscape and the specific risk profile of the organisation. - Executing a Targeted Remediation Plan: From KEV Analysis to Action
With a prioritisation strategy in place, the execution of a targeted remediation plan is crucial. I detailed the process of translating vulnerability analysis into actionable steps for mitigation, emphasising the importance of focusing on vulnerabilities identified as being actively exploited. This targeted approach ensures that remediation efforts are strategic, impactful, and aligned with the organisation’s risk priorities. - Staying Ahead of the Curve: Monitoring CVE Exploitability Changes
The dynamic nature of cybersecurity threats necessitates continuous vigilance. I highlighted the importance of monitoring changes in CVE exploitability to adjust remediation priorities accordingly. Staying informed about the latest developments enables organisations to proactively address emerging threats and adapt their defensive strategies in response to the evolving threat environment. - Beyond NIST: Diversifying Sources for Accurate Vulnerability Context
I advocated for expanding beyond the NIST National Vulnerability Database to incorporate a broader spectrum of vulnerability intelligence sources. This approach provides a more comprehensive and contextual understanding of vulnerabilities, enhancing the accuracy of risk assessments and the effectiveness of remediation strategies. - Communicating Vulnerability Risks: Translating Technical Jargon into Business Impact
Effective communication between security teams and business stakeholders is critical. I discussed strategies for translating technical details of vulnerabilities into terms that resonate with business priorities. By effectively conveying the potential impact of vulnerabilities on business operations and objectives, security professionals can facilitate informed decision-making and ensure that remediation efforts are aligned with the organisation’s strategic goals.
Through these articles, I’ve shared my journey and insights into enhancing cybersecurity strategies. Each piece offers a deeper understanding of the critical components of vulnerability management, aiming to empower organisations to navigate the complexities of cybersecurity with confidence and strategic acumen.

